Password attacks fall under the category of espionage or trespass just as lock picking falls under breaking and entering. Attempting to guess or reverse-calculate a password is often called cracking. There are several alternative approaches to password cracking, these include:
- Brute force
- Dictionary
- Rainbow tables
- Social engineering
The application of computing and network resources to try every possible password combination is called a brute force password attack. If attackers can narrow the field of target accounts, they can devote more time and resources to these accounts. This is one reason to always change the password of the manufacturer’s default administrator account.
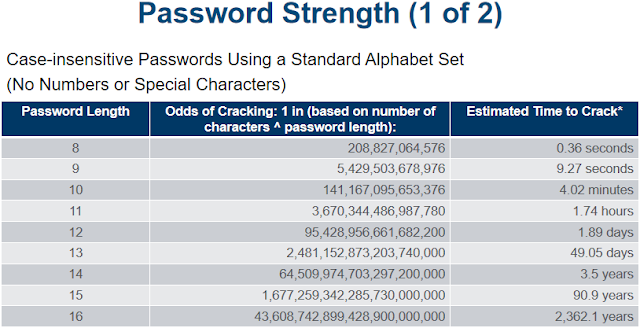
Brute force password attacks are rarely successful against systems that have adopted the manufacturer’s recommended security practices. Controls that limit the number of unsuccessful access attempts within a certain time are very effective against brute force attacks. As shown in Table 2 dash 6, the strength of a password determines its ability to withstand a brute force attack. Using best practice policies like the 10.4 password rule and systems that allow case-sensitive passwords can greatly enhance their strength.
The dictionary password attack, or simply dictionary attack, is a variation of the brute force attack that narrows the field by using a dictionary of common passwords and includes information related to the target user, such as names of relatives or pets, and familiar numbers such as phone numbers, addresses, and even Social Security numbers. Organizations can use similar dictionaries to disallow passwords during the reset process and thus guard against passwords that are easy to guess. In addition, rules requiring numbers and special characters in passwords make the dictionary attack less effective.
A far more sophisticated and potentially much faster password attack is possible if the attacker can gain access to an encrypted password file, such as the Security Account Manager (SAM) data file. While these password files contain hashed representations of users’ passwords—not the actual passwords, and thus cannot be used by themselves—the hash values for a wide variety of passwords can be looked up in a database known as a rainbow table. These plain text files can be quickly searched, and a hash value and its corresponding plaintext value can be easily located. Module 10, “Cryptography,” describes plaintext, ciphertext, and hash values in greater detail.
While social engineering is discussed in detail later in the section called “Human Error or Failure,” it is worth mentioning here as a mechanism to gain password information. Attackers posing as an organization’s IT professionals may attempt to gain access to systems information by contacting low-level employees and offering to help with their computer issues. After all, what employee doesn’t have issues with computers? By posing as a friendly help-desk or repair technician, the attacker asks employees for their usernames and passwords, and then uses the information to gain access to organizational systems. Some even go so far as to resolve the user’s issues. Social engineering is much easier than hacking servers for password files.



I caught my husband so many times through his chats and all about cheating on me and when i told him he always claims that he has changed and all..right now he hides his phone from me and i still guess he is cheating cause i could not break into his phone any more so i was referred to a hacker named Henry Clark who i ran to for help and this hacker was able to break into his phone and proved me with the access to my husband phone without my spouse knowing about the hack..right in my phone i have all my husband phone daily activities in my phone i got to read all his chats, text, calls, whats-app, Facebook, and many more this hacker is really great thank you.
ReplyDeleteDid you find this review helpful? contact him via gmail, Henryclarkethicalhacker@gmail.com and you can text, call and whatsapp him on +1813-421-1326..
Tested and trusted..
iuyyy