Many public and private organizations promote solid best security practices. Professional societies often provide information on best practices for their members. The Technology Manager’s Forum (www.techforum.com) has an annual best practice award in several areas, including information security. The Information Security Forum (www.securityforum.org) has a free publication titled “Standard of Good Practice for Information Security,” which outlines information security best practices.
Many organizations hold seminars and classes on best practices for implementing security; in particular, the Information Systems Audit and Control Association (www.isaca.org) hosts regular seminars. The International Association of Professional Security Consultants (www.iapsc.org) has a listing of best practices. At a minimum, information security professionals can peruse Web portals for posted security best practices. Several free portals dedicated to security have collections of best practices, such as SearchSecurity.com and NIST’s Computer Resources Center.
To inform the discussion of information security program architecture and to illustrate industry best practices, the following sections outline a few key components of security architecture. Many of these components are examined in detail in later modules of the book, but this overview can help you assess whether a framework and blueprint are on target to meet an organization’s needs.
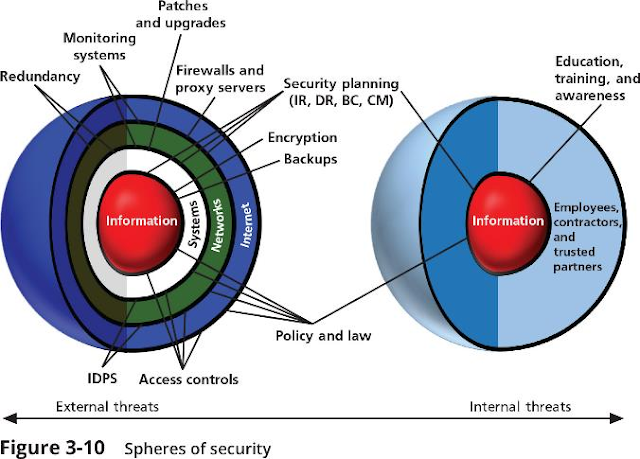
The spheres of security, shown in Figure 3-10, are the foundation of the security framework. Generally speaking, the spheres of security illustrate how information is under attack from a variety of sources. The right side of Figure 3-10 illustrates the ways in which internal users access information. For example, users can access hard copies of documents and information directly. Information, as the most important asset in this model, is at the center of the sphere. Information is always at risk from attacks whenever it is accessible by people or computer systems. Networks and the Internet are indirect threats, as exemplified by the fact that a person attempting to access information from the Internet must traverse local networks.
The left side of Figure 3-10 illustrates that a layer of protection must exist between each layer of the sphere of use. For example, “Policy and law” and “Education and training” are protections placed between people and the information. Controls are also implemented between systems and the information, between networks and the computer systems, and between the Internet and internal networks. This reinforces the concept of defense in depth. A variety of controls can be used to protect the information. The items of control shown in the figure are not intended to be comprehensive, but they illustrate some of the safeguards that can protect the systems closer to the center of the sphere. Because people can directly access each ring as well as the information at the core of the model, the side of the sphere of protection that attempts to control access by relying on people requires a different approach to security than the side that uses technology. The members of the organization must become a safeguard that is effectively trained, implemented, and maintained, or they too will present a threat to the information.
Information security is designed and implemented in three layers: policies, people (education, training, and awareness programs), and technology. These layers are commonly referred to as PPT. Each layer contains controls and safeguards to protect the information and information system assets that the organization values. But, before any technical controls or other safeguards can be implemented, the policies that define the management philosophies behind the security process must be in place.
Levels of Controls
Information security safeguards provide three levels of control: managerial, operational, and technical. Managerial controls set the direction and scope of the security process and provide detailed instructions for its conduct. In addition, these controls address the design and implementation of the security planning process and security program management. They also address risk management and security control reviews (as described in Module 4), describe the necessity and scope of legal compliance, and set guidelines for the maintenance of the entire security life cycle.
Operational controls address personnel security, physical security, and the protection of production inputs and outputs. In addition, operational controls guide the development of education, training, and awareness programs for users, administrators, and management. Finally, they address hardware and software systems maintenance and the integrity of data.
Technical controls are the tactical and technical implementations of security in the organization. While operational controls address specific operating issues, such as developing and integrating controls into the business functions, technical controls include logical access controls, such as identification, authentication, authorization, accountability (including audit trails), cryptography, and the classification of assets and users.
A basic tenet of security architectures is the layered implementation of security. To achieve defense in depth, an organization must establish multiple layers of security controls and safeguards, which can be organized into policy, training and education, and technologies, as shown in the CNSS model presented in Module 1. While policy itself may not prevent attacks, it certainly prepares the organization to handle them; when coupled with other layers, policy can deter attacks. For example, the layer of training and education can help defend against attacks enabled by employee ignorance and social engineering. Technology is also implemented in layers, with detection equipment working in tandem with reaction technology behind access control mechanisms. Redundancy can be implemented at several points throughout the security architecture, such as in firewalls, proxy servers, and access controls. Figure 3-11 illustrates the concept of building controls in multiple and sometimes redundant layers. The figure shows firewalls and prevention IDPSs that use both packet-level rules (shown as the packet header in the diagram) and content analysis (shown as a database icon with the caption 0100101011). More information on firewalls and intrusion detection systems is presented in Modules 8 and 9, respectively.
A perimeter is a boundary of an area. A security perimeter is the border of security that protects all internal systems from outside threats, as pictured in Figure 3-12. Unfortunately, the perimeter does not protect against internal attacks from employee threats or on-site physical threats. In addition, the emergence of mobile computing devices, telecommuting, and cloud-based functionality has made the definition and defense of the perimeter increasingly more difficult. This has led some security experts to declare the security perimeter extinct and call for an increased focus on improved system-level security and active policing of networked assets. An organization can have both an electronic security perimeter, usually at the exterior network or Internet connection, and a physical security perimeter, usually at the entrance to the organization’s offices. Both require perimeter security. Security perimeters can effectively be implemented as multiple technologies that segregate the protected information from potential attackers. Within security perimeters, the organization can establish security domains, each with differing levels of security, between which traffic must be screened. The assumption is that if people have access to one system within a security domain, they have authorized access to all systems within that domain. The security perimeter is an essential element of the overall security framework, and its implementation details are the core of the completed security blueprint. The key components of the security perimeter are firewalls, DMZs (demilitarized zones), proxy servers, and IDPSs. You will learn more about information security technologies in Modules 8, 9, and 10.
Many security experts argue that the security perimeter is dead. With the dramatic growth in popularity of cloud-based computing and data storage, and the continued use of mobile computing devices, they argue that there is no “inside” or “outside” to organizations’ networks anymore. Whether this is true is the subject of much debate. With the extensive use of cloud-based services to deliver key systems capability, including security-related functions, there is a growing movement toward realizing that a security perimeter is the entirety of an organization’s network presence, anywhere and everywhere the company’s data is, and that the use of defense in depth is still a valid approach to protecting it. Whether you subscribe to the “perimeter is dead” philosophy or not, the responsibility for protecting the organization’s data using every available resource is still alive and well.
Janet stood up from the conference table and left the room.
The meeting had not lasted long, considering how significant its impact would be on Janet’s life. Two officers from the corporate security team waited in the hallway to walk her to her office and collect her personal possessions, which were already in a box at her administrative assistant’s desk. Her access card, phone, tablet, and laptop were already turned in, and every password she had ever used at SLS had been deactivated.
She was not looking forward to explaining this to her family.
The meeting in the room continued.
Fred asked, “Are we sure this was our only course? This seems harsh to me.”
Janet’s superior, the senior vice president of marketing, nodded and said, “I have to say that I agree. Janet was a solid performer and will be difficult, and expensive, to replace.”
Charlie added, “I know what you mean. Jamie Hyack, the network engineer, is the same, except he chose to enable Janet’s network access for her rotisserie league server without approval, without change control, and putting the company’s entire network at risk. He had to go.”
Gladys took a breath and said, “Sadly, this was needed. We cannot have two tiers of enforcement in our application of policy. If we do not enforce this policy requirement on executives, how can we be expected to have compliance from other employees?”
She continued, “As Charlie pointed out when we decided on this course of action, we have to enforce the policy we have in place. We can make changes to it that we feel better about and enforce those changes in the future.”
Discussion Questions
- Does this application of policy seem harsh to you? What alternatives might be implemented in policy to make it enforceable and perhaps less stringent than in this example?
- Are there other punishments that might be enacted for situations like this? How might you propose structuring the policy to clarify what levels of punishment are appropriate?
Ethical Decision Making
The policies that organizations put in place are similar to laws, in that they are directives for how to act properly. Like laws, policies should be impartial and fair, and are often founded on ethical and moral belief systems of the people who create them.
In some cases, especially when organizations expand into foreign countries, they experience a form of culture shock when the laws of their new host country conflict with their internal policies. For example, suppose that SLS has expanded its operations into France. Setting aside any legal requirements that SLS make its policies conform to French law, does SLS have an ethical imperative to modify its policies across the company in all of its locations to better meet the needs of its stakeholders in the new country?
Suppose SLS has altered its policies for all operations in France and that the changes are much more favorable to employees—such as a requirement to provide childcare and eldercare services at no cost to employees. Is SLS under any ethical burden to offer the same benefit to employees in its home country?







0 comments:
Post a Comment